CableBeachProposal
From OpenSimulator
m (Robot: Cosmetic changes) |
|||
| (8 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
| + | __NOTOC__ | ||
| + | {{Quicklinks}} | ||
| + | |||
{{proposal}} | {{proposal}} | ||
| − | =Cable Beach Proposal= | + | = Cable Beach Proposal = |
| − | ==Motivation== | + | == Motivation == |
Many virtual worlds are being developed independently with a wide variety of different architectures and protocols. The current generation of virtual worlds are implemented as proprietary stacks of services, where each world is not only simulating virtual space but also providing identity services, content hosting, digital rights management, instant messaging, virtual economies, social networking elements such as groups, and many other services. We believe there are shortcomings with this approach. Specifically: | Many virtual worlds are being developed independently with a wide variety of different architectures and protocols. The current generation of virtual worlds are implemented as proprietary stacks of services, where each world is not only simulating virtual space but also providing identity services, content hosting, digital rights management, instant messaging, virtual economies, social networking elements such as groups, and many other services. We believe there are shortcomings with this approach. Specifically: | ||
| − | # The barrier to entry for creating and running a virtual world is too high. Even with popular platforms such as OpenSim, | + | # The barrier to entry for creating and running a virtual world is too high. Even with popular platforms such as OpenSim, virtual world administrators are taking on a monumental task of overseeing many or all of the above services when only a simple world simulation is needed. |
# The all-or-nothing approach of the current protocols prevents the development of a robust virtual world ecosystem, where many specialized services are provided. Today's large stakeholders in content hosting, content delivery acceleration, identity services, and social networking have no means of entry to the virtual worlds space. | # The all-or-nothing approach of the current protocols prevents the development of a robust virtual world ecosystem, where many specialized services are provided. Today's large stakeholders in content hosting, content delivery acceleration, identity services, and social networking have no means of entry to the virtual worlds space. | ||
# Due to the walled garden nature of current worlds, third party services such as search and digital content creation tools have been almost entirely locked out of virtual worlds. | # Due to the walled garden nature of current worlds, third party services such as search and digital content creation tools have been almost entirely locked out of virtual worlds. | ||
| − | ==Vision== | + | == Vision == |
| − | We envision virtual | + | We envision virtual worlds modeled after the current World Wide Web, with millions of independent administrative domains. Content will be spread across millions of small, independent domains as well as aggregated on large domains supporting millions of users. A rich community of value added services and the free and open exchange of content will weave the network together, much as the Web 2.0 movement is tying the web together today. Every organization can choose what services they will run themselves, what services will be provided by third parties, and which third parties will provide services. Additionally, the content rights decisions are placed in the hands of the content hosts. With the proper authentication users are free to move assets to wherever they roam. |
Data services will become as important as data hosting itself. Just as search engines and content portals have changed how we use the web, services that can plug into a common interface in asset hosting will change how we use virtual worlds. Auditing services can provide an approach to rights management and traffic analytics. Existing caching techniques and services that have been built for today's web content can be leveraged for delivery of rich virtual world content. | Data services will become as important as data hosting itself. Just as search engines and content portals have changed how we use the web, services that can plug into a common interface in asset hosting will change how we use virtual worlds. Auditing services can provide an approach to rights management and traffic analytics. Existing caching techniques and services that have been built for today's web content can be leveraged for delivery of rich virtual world content. | ||
| − | ==Overview== | + | == Overview == |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | Cable Beach is a service based architecture. Every category of functionality in a virtual world is designated as a service. The services can be organized in any number of different ways and spread across different processes, different servers, or different trust domains. In fact, several services can collectively provide a rich experience with complex interactions while still operating completely independently of one another. | |
| − | + | ||
| − | + | The following diagram shows an overview of the Cable Beach architecture divided up into trust domains. Everything operating inside of a trust domain has some implicit level of trust for all of the other members of the trust domain, although that level of trust will vary depending on the purpose of the trust domain and the policy put in place for that domain. | |
| − | + | [[File:Cablebeach-trustoverview.png]] | |
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | + | ||
| − | === | + | === World Domain === |
| − | + | ||
| − | + | All of the services responsible for simulating a virtual world fall under the umbrella of the world domain. The ultimate authority of this domain is the world service, which acts as both the gatekeeper for incoming clients and oversees all of the simulation nodes in the world. All clients wishing to connect to this world should connect through the world server, which will enforce global policy such as access lists. The trust requirements of the world domain are not defined by the architecture, but rather the policies of each world. In other words, the level of trust services in the world domain have for each other is entirely dependent on the world policies. Some worlds might choose a very tight controlled policy to facilitate the safety of online transactions, while other worlds might choose a very open membership policy. The mechanisms and policies used to establish trust between services inside the world domain is out of the scope of this architecture. | |
| − | + | === Identity === | |
| − | + | Identity is not tied to a particular world. Instead, identity is treated as an independent service, allowing any client to attempt to login to any world. Which logins will actually be allowed are defined by policy of the world service. The closed world of fantasygameworld.com might provide its own identity server at users.fantasygameworld.com and only accept logins from identities at that domain. Another world might default to allowing logins from anywhere, but blacklist specific domains such as virtualspammers.com. The external identity service abstracts the security requirements for worlds away from the architectural design and allows a wide variety of policy decisions for clients to be enforced. | |
| − | + | ||
| − | + | In the Cable Beach architecture, identity is more than just a URL identifier. A list of attributes are attached to each identity that provide the metadata necessary to simulate the presence of an identity in a virtual world. Attribute types are defined by URLs, similar to OpenID Attribute Exchange. Each attribute stores LLSD; the format of the LLSD is specific to the attribute. As an example, an identity might have first name and last name attributes of the string type. Some attributes are references to the URL of a service, such as inventory or messaging. Some attributes will naturally be closely tied to the identity itself, such as the avatar name. Other attributes may be specific to a particular world, such as a high score or a list of completed quests. World services may request any list of attributes from an identity service, as well as supplementing the list with additional avatar attributes stored in the world service. | |
| − | + | === Services === | |
| − | + | In addition to data attributes such as avatar name, some attributes store service URLs. When a client contacts a world service to log in, the world service compiles a list of required services and service capabilities that will be used during the client session in this world. While the communication between the world service and trusted services outside of the scope of this architecture, communication between the world service and untrusted services is well defined to ensure interoperability. The OAuth protocol is used to allow third party services to independently confirm the client identity and then confirm the list of required capabilities with the client. Once authentication and authorization have been confirmed, the world service uses the OAuth authorization token to retrieve temporary capability URLs for each requested capability. | |
| − | + | Any number of services can be attached to an identity. Some services such as inventory might be very common across many worlds, while world-specific services such as a trophy server might apply to a very small subset of worlds or even a single world. For example, fantasygameworld.com may associate a trophy service with all incoming clients to track progress and achievements in that world. Inventory may be restricted to items only found in fantasygameworld.com by ignoring external inventory services and associating an internal inventory service with each identity. Future revisions may support multiple services for the same service type, such as accessing an internal and external inventory service simultaneously. | |
| − | == | + | == Prototype == |
| − | + | The prototype implementation of Cable Beach is designed in a modular way to support centralized and decentralized concepts simultaneously. For example, the WorldServer can also act as an identity service to provide a login path for XML-RPC requests (using username and password combination) from the current Second Life client. Client authentication can be skipped in the InventoryServer, making the assumption that the WorldServer and InventoryServer exist in the same trust domain and only the WorldServer has access to the InventoryServer OAuth endpoint. This gives existing virtual worlds the immediate benefit of a more flexible service architecture while remaining backward compatible with the current login flow. Client modifications are being developed to allow the existing Second Life viewer to participate in completely decentralized grids. | |
Latest revision as of 20:44, 3 March 2012
| This article or section is a Proposal It does not represent the current state of OpenSim, but is an idea for future work in OpenSim. Please feel free to update this page as part of the proposal discussion. |
[edit] Cable Beach Proposal
[edit] Motivation
Many virtual worlds are being developed independently with a wide variety of different architectures and protocols. The current generation of virtual worlds are implemented as proprietary stacks of services, where each world is not only simulating virtual space but also providing identity services, content hosting, digital rights management, instant messaging, virtual economies, social networking elements such as groups, and many other services. We believe there are shortcomings with this approach. Specifically:
- The barrier to entry for creating and running a virtual world is too high. Even with popular platforms such as OpenSim, virtual world administrators are taking on a monumental task of overseeing many or all of the above services when only a simple world simulation is needed.
- The all-or-nothing approach of the current protocols prevents the development of a robust virtual world ecosystem, where many specialized services are provided. Today's large stakeholders in content hosting, content delivery acceleration, identity services, and social networking have no means of entry to the virtual worlds space.
- Due to the walled garden nature of current worlds, third party services such as search and digital content creation tools have been almost entirely locked out of virtual worlds.
[edit] Vision
We envision virtual worlds modeled after the current World Wide Web, with millions of independent administrative domains. Content will be spread across millions of small, independent domains as well as aggregated on large domains supporting millions of users. A rich community of value added services and the free and open exchange of content will weave the network together, much as the Web 2.0 movement is tying the web together today. Every organization can choose what services they will run themselves, what services will be provided by third parties, and which third parties will provide services. Additionally, the content rights decisions are placed in the hands of the content hosts. With the proper authentication users are free to move assets to wherever they roam.
Data services will become as important as data hosting itself. Just as search engines and content portals have changed how we use the web, services that can plug into a common interface in asset hosting will change how we use virtual worlds. Auditing services can provide an approach to rights management and traffic analytics. Existing caching techniques and services that have been built for today's web content can be leveraged for delivery of rich virtual world content.
[edit] Overview
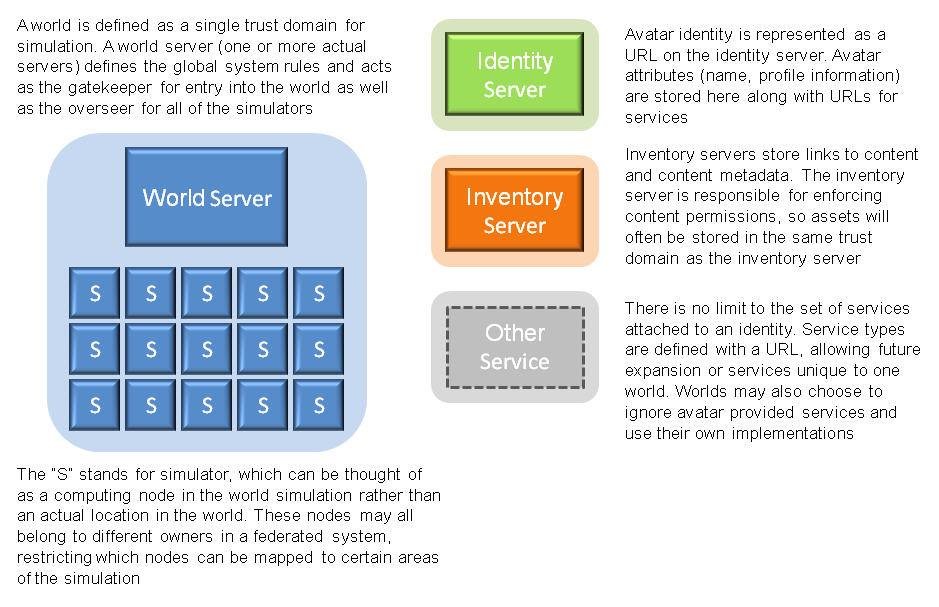
Cable Beach is a service based architecture. Every category of functionality in a virtual world is designated as a service. The services can be organized in any number of different ways and spread across different processes, different servers, or different trust domains. In fact, several services can collectively provide a rich experience with complex interactions while still operating completely independently of one another.
The following diagram shows an overview of the Cable Beach architecture divided up into trust domains. Everything operating inside of a trust domain has some implicit level of trust for all of the other members of the trust domain, although that level of trust will vary depending on the purpose of the trust domain and the policy put in place for that domain.
[edit] World Domain
All of the services responsible for simulating a virtual world fall under the umbrella of the world domain. The ultimate authority of this domain is the world service, which acts as both the gatekeeper for incoming clients and oversees all of the simulation nodes in the world. All clients wishing to connect to this world should connect through the world server, which will enforce global policy such as access lists. The trust requirements of the world domain are not defined by the architecture, but rather the policies of each world. In other words, the level of trust services in the world domain have for each other is entirely dependent on the world policies. Some worlds might choose a very tight controlled policy to facilitate the safety of online transactions, while other worlds might choose a very open membership policy. The mechanisms and policies used to establish trust between services inside the world domain is out of the scope of this architecture.
[edit] Identity
Identity is not tied to a particular world. Instead, identity is treated as an independent service, allowing any client to attempt to login to any world. Which logins will actually be allowed are defined by policy of the world service. The closed world of fantasygameworld.com might provide its own identity server at users.fantasygameworld.com and only accept logins from identities at that domain. Another world might default to allowing logins from anywhere, but blacklist specific domains such as virtualspammers.com. The external identity service abstracts the security requirements for worlds away from the architectural design and allows a wide variety of policy decisions for clients to be enforced.
In the Cable Beach architecture, identity is more than just a URL identifier. A list of attributes are attached to each identity that provide the metadata necessary to simulate the presence of an identity in a virtual world. Attribute types are defined by URLs, similar to OpenID Attribute Exchange. Each attribute stores LLSD; the format of the LLSD is specific to the attribute. As an example, an identity might have first name and last name attributes of the string type. Some attributes are references to the URL of a service, such as inventory or messaging. Some attributes will naturally be closely tied to the identity itself, such as the avatar name. Other attributes may be specific to a particular world, such as a high score or a list of completed quests. World services may request any list of attributes from an identity service, as well as supplementing the list with additional avatar attributes stored in the world service.
[edit] Services
In addition to data attributes such as avatar name, some attributes store service URLs. When a client contacts a world service to log in, the world service compiles a list of required services and service capabilities that will be used during the client session in this world. While the communication between the world service and trusted services outside of the scope of this architecture, communication between the world service and untrusted services is well defined to ensure interoperability. The OAuth protocol is used to allow third party services to independently confirm the client identity and then confirm the list of required capabilities with the client. Once authentication and authorization have been confirmed, the world service uses the OAuth authorization token to retrieve temporary capability URLs for each requested capability.
Any number of services can be attached to an identity. Some services such as inventory might be very common across many worlds, while world-specific services such as a trophy server might apply to a very small subset of worlds or even a single world. For example, fantasygameworld.com may associate a trophy service with all incoming clients to track progress and achievements in that world. Inventory may be restricted to items only found in fantasygameworld.com by ignoring external inventory services and associating an internal inventory service with each identity. Future revisions may support multiple services for the same service type, such as accessing an internal and external inventory service simultaneously.
[edit] Prototype
The prototype implementation of Cable Beach is designed in a modular way to support centralized and decentralized concepts simultaneously. For example, the WorldServer can also act as an identity service to provide a login path for XML-RPC requests (using username and password combination) from the current Second Life client. Client authentication can be skipped in the InventoryServer, making the assumption that the WorldServer and InventoryServer exist in the same trust domain and only the WorldServer has access to the InventoryServer OAuth endpoint. This gives existing virtual worlds the immediate benefit of a more flexible service architecture while remaining backward compatible with the current login flow. Client modifications are being developed to allow the existing Second Life viewer to participate in completely decentralized grids.